development
software
risk
secure
Security in Software Development - Risks, Practices, and More

Everyone knows perfectly well that safety is the most important thing. The problem is that not many cares. Hence, numerous dangers and unforeseen accidents could have been avoided if someone had taken care of it in advance.
Durable and Secure Software Development is not easy to achieve, which is why many turn to the help of specialists. If this is an option that interests you, be sure to read our article "Why do Companies Outsource IT Projects?" in which we describe the reasons and benefits of outsourcing projects to experienced contractors.
If you want to do it yourself, you must know that software developers and software development companies like us must follow established standards when writing code. It doesn't matter if you aim to create a cross-platform application with Angular development services to create a stunning website or focus on native app development with React Native development services to make a bestseller mobile app. Security risks can lurk anywhere. These best practices aim to reduce any potential security flaws in your code, safeguard it against hackers and cybercriminals, and preserve user privacy.
This article will explain to you why you should take care of security in your project and provide a list of essential best practices for building secure software programs.
What is Secure Software Development?
The phrase "secure software development" refers to the process of developing software that incorporates security into every stage of the software development lifecycle (SDLC). Rather than trying to fix problems after testing reveals critical product flaws, secure software development is a technique for generating code that includes security from start to finish. The term implies that security is incorporated into the planning phase long before a single line of code is written.
Does SLDC mean something else? Yes, it is a process full of phases of specific actions that cannot be explained in a few sentences. Fortunately, we have prepared an article about the software development life cycle from which you can learn what the phases are in it, what they contain, what is the goal of SLDC and much more. It is worth learning more about SLDC to understand the recipe for secure software development better.
Traditionally, developers have seen security as a roadblock to innovation and creativity, resulting in delays in bringing the product to market. This thinking harms a company's profits because bug fixes during implementation are six times more costly, and bug repairs during testing are 15 times more expensive than fixing the same problem early in the design process.
Finally, how pleased will customers be with a product's innovative features if it is rife with vulnerabilities that hackers may use to exploit? Today, security must take precedence in the software engineering process, and those who do not comply will struggle to compete.
Software Development Biggest Risks

Understanding software developers' most prevalent security concerns are critical before going through the best practices. The following are some of the most frequent security risks encountered by software designers:
Legacy Software
Legacy applications are vulnerable to cyber-attacks and data breaches. They are frequently developed without secure coding techniques. They aren't updated regularly, making them vulnerable to cyber-attacks and data breaches.
Bad Maintenance
The software probably has vulnerabilities if you have stopped developing your application or are only being supported by a small team. If these weaknesses are taken advantage of, hackers could access secure data and confidential information stored on your server, resulting in various security concerns.
Discontinuing or neglecting security testing or other maintenance practices is asking for trouble and increasing the chance that something bad will happen to your project.
Poor Code
Inadequate testing is another typical software development hazard. Insecure code is challenging to secure, and coding procedures such as input validation, output encoding, error handling, secure storage, and secure coding techniques are frequently neglected.
The simple code does not mean it is easy to secure, exposing sensitive data to the wrong individuals. Later on, we distinguish secure coding practices, so you can be sure that your code is secure enough to avoid that risk.
Vulnerability of Web Services
Web services frequently store the user's personal information and sensitive data. As a web application development company, we are alert that hackers may use web services' vulnerabilities to access private information or carry out illegal activities on your website if they exist.
That storage problem also affects passwords. Use strong cryptography to keep your passwords secure. Passwords are stored in an easily accessible format, making it simple for our threatening methods, such as dictionary and brute force attacks, to steal and decipher them.
Building a Secure Software Development

In the past, people would rarely think about security in software development and only consider it during the testing phase. However, new methodologies like Agile include ongoing testing for secure software development in every stage of SDLC.
The vulnerabilities of software systems are always being sought out and exploited by hackers and cybercriminals. Developers and stakeholders have more possibilities to troubleshoot potential security issues early on and correct them as part of the software development process if security is prioritized throughout the SDLC. Are you not familiar with the agile methodology? It is definitely worth getting to know this method. One of the ways is to read our article, in which you will learn what it is and why it is worth being aware of the Agile method.
By integrating software development security principles and continuous testing efforts throughout the SDLC, organizations can avoid the costly process of having to test and patch up security gaps overnight before release.
Software testing should not be a one-time reactionary activity. If you want to avoid running into costly software flaws, don't forget to include basic foundation building throughout the design development process.
Software Development Life Cycle
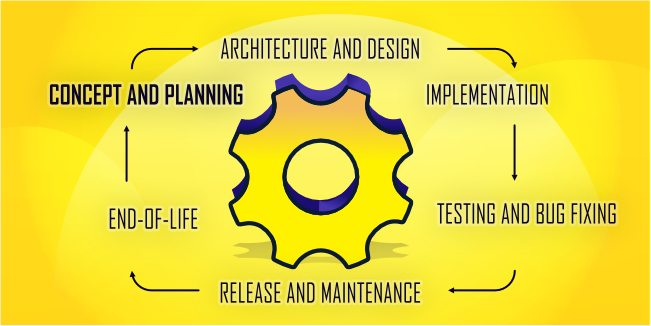
Most strategies that improve application security are most effective at particular periods. It is why it's critical to prepare ahead of time. Here, secure development methods - also known as SDLCs - come in handy: they instruct you on what to do and when to do it.
The subsequent paragraphs will outline these software development phases and the corresponding SDL suggestions.
Concept and Planning
This stage aims to formalize the application concept and assess its viability. It includes working out a project strategy, defining requirements, and allocating human resources.
The recommended SDL practices for this stage include:
- SDL Discovery - The SDL discovery process begins with creating security and compliance goals for your project. Then choose an SDL approach and develop a thorough strategy for carrying out all needed SDL activities. It ensures that your staff will begin addressing security issues as soon as possible.
- Security Requirements - By preparing a list of security requirements for your project, you can more easily identify and fix areas that do not comply with regulations. Include both technical and regulatory requirements on this list.
- Security Awareness Training - Training sessions provide knowledge on security, from beginner lessons like threat awareness to more complex topics like secure development. All project participants can establish a security mindset by starting with the basics. The advanced courses build upon this foundation by teaching design principles to critical team members.
These techniques make it more likely that your project will succeed and that your application will meet security standards. This stage also assigns the required personnel with a background in application security.
Architecture and Design
This stage aims to model a product that adheres to the requirements, which entails envisioning the application structure and how it will be used and selecting ready-made components from external sources that will save time during development. The outcome of this phase is a comprehensive design document.
The following SDL practices are recommended for this stage:
- Cyber-threat Modeling - Threat modeling is the process of assessing potential attack methods and incorporating corresponding defenses into the application design. Modeling uncovers possible hazards early, lowering associated expenses and establishing the groundwork for future incident response strategies.
- Secure Design - The design document and subsequent changes are verified against security standards. Early design reviews aid in the detection of security vulnerabilities before they are implemented.
- Third-party Software Tracking - By examining third-party software frequently, security teams can locate compromised components that might otherwise go unnoticed. It allows them to fix vulnerabilities before they result in a data breach or system malfunction.
By adopting these practices, you can prevent weaknesses from appearing in your application. Checking compliance also decreases security risks and the likelihood of vulnerabilities originating from third-party components.
Implementation
It is the phase where an application becomes a reality. This process involves writing code for the app, debugging it, and finally creating builds that are good enough to test.
Some of the SDL methods recommended for this stage are:
- Secure Coding - Checklists and guides are crucial for developers as they remind them of common mistakes, such as unencrypted passwords. If secure coding practices principles are upheld, many vulnerabilities can be avoided, and more time can be spent on other tasks.
- Static Scanning - Static application scanning tools (SAST) save time by thoroughly examining code for weaknesses and red flags before running the application. Additionally, using SASTs daily prevents coding errors from slipping through the cracks.
- Code Review - Manually reviewing code is essential to developing secure applications, even though automated scanning can save a lot of work. If done promptly, developers can catch and correct potential problems before they start working on something else.
By implementing these practices, you can decrease the number of security issues. For optimal results, automatic scanning should be done with manual reviews.
Testing and Bug Fixing
This phase is intended to find and fix application errors. It includes running automated and manual tests and identifying and resolving problems.
Follow these techniques:
- Dynamic Scanning - DAST works by ransomware hacker attacks to find weak spots. But, to lower false positives, a combined approach is more effective (IAST). This method monitor executed code and application data flow in addition to runtime scanning. Dynamic scanning finds not only common vulnerabilities but also configuration errors that would reduce security.
- Fuzzing - Fuzz testing is a generic term for any test that makes random data based on unique patterns and determines whether the app can properly handle such data. Automated fuzzing tools help to prevent SQL injection attacks by detecting malformed inputs.
- Penetration Testing - Using a third-party group of security experts to perform phony assaults is a good idea. External experts rely on their expertise and instinct to re-create possible attacks that your team might have missed.
These methods, when followed consistently, help to prevent the emergence of new problems. It provides good protection against a wide range of known dangers, thanks to the techniques from the previous stages.
Release and Maintenance
At this point, a program is live, with many copies running in various conditions. New versions and patches are eventually released, and some consumers choose to upgrade while others prefer to maintain the older versions.
SDL practices recommended for this stage include:
- Environment Management - Environmental configuration errors and vulnerabilities continue to plague many systems. However, you can drastically improve its security by monitoring the system as a whole and not just focusing on the application.
- Incident Response Plan - A security incident response plan specifies the procedures your incident team must follow to address any security breaches that may occur. The response plan must be implemented quickly for triage and repair of cyber attacks.
- Ongoing Security Checks - Because researchers are finding new ways for attacks regularly, it's crucial to do security checks frequently. It will protect your application from any potential threats.
We can respond quickly and effectively to emerging threats by adopting these practices.
End-Of-Life
"End of life" refers to when software is no longer supported by its developer. It may present issues for applications that store private data, as they could be subject to certain end-of-life regulations.
At this stage, we recommend the following SDL activities:
- Data Retention - Governments regulate some data types. Check whether your firm's retention policies conform with legal standards, which may reduce the chance of hefty fines.
- Data Disposal - At the end of the life of a program, all sensitive data stored within it must be deleted securely. Encryption keys and personal information are two examples of this type of data. Data removal after a project assures privacy and protects from data breaches by ensuring that such data is destroyed safely.
Developers utilize these strategies to ensure adequate time to write regulations-compliant policies.
Secure Software Development Practices

In today's increasingly dangerous threat environment, producing safe software is difficult, but it couldn't be more essential as more successful software-linked assaults make headlines.
As a result, we put up a list of ten software development best practices to assist you in developing the safest possible software and avoiding becoming a data cybercrime statistic. So, here they are, our top ten software security development best practices:
Security From The Start
Security should be part of your culture and code, and there's no better place to start than in the earliest development phase. Before you begin coding, plan how you will integrate security into every stage of the software development life cycle. From day one, use automation to test for and monitor vulnerabilities.
Hire Professionals
You can use the best techniques and methods to write good and safe code, but when you are not up-to-date, and writing code is not your strong point, it is worth delegating this task to specialists.
A qualified offshore outsourcing company can work wonders. They will not only write a code that will meet your expectations, but it will also be safe, readable, and reliable. They will be maintaining it all the time. They will introduce the necessary changes and improve it along with the latest developments in the industry.
Create a Secure Software Development Policy
It will guide you on readying your team, processes, and technology for secure software development. This policy gives specific directions for approaching and adding security features in each stage of the SDLC. Furthermore, it provides the governing rules and roles to help reduce vulnerability risk during software production.
Employ a Secure Software Development Framework
Let's stop for a moment here and explain what a Secure Software Development Framework is.
The Secure Software Development Framework (SSDF) provides reliable and secure practices for software development based on documents from credible organizations such as BSA, OWASP, and SAFECode. Even though few models for the software development life cycle (SDLC) mention software security explicitly, adding SSDF's best practices to your SDLC implementation will leave you feeling confident.
A well-structured and consistent framework like NIST SSDF will provide structure and uniformity to your team's efforts in following sound software security practices. Frameworks can assist with the "What are we going to do now?" question, as well as all new software developers.
Adapt Practices You've Learned To Your Software
Clearly state all security guidelines and inform your developers to code using only secure techniques that follow these guidelines. Ensure that all of your outside vendors are aware of your company's security standards and confirm that they can meet them; if not, this could open an attack.
Protect Code Integrity
Maintaining code security is key to preventing tampering. Code signing should be closely monitored and regulated to preserve integrity. Keep all code in repositories that only authorized personnel can access.
Review and Test Code
Avoid the trap of following a conventional SDLC development pattern and testing code toward the end of the process. Instead, continually use developer evaluations and automated testing to check code for flaws. Early detection of vulnerabilities saves money and time while reducing developer aggravation later.
Be Prepared to Mitigate Vulnerabilities Quickly
Vulnerabilities are a given in software development. It's not if they'll happen, but when, so be prepared to deal with problems in real-time with a team, a strategy, and procedures. Remember that the sooner you can detect and address security flaws, the better (i.e., limiting the window of vulnerability).
Configure Secure Default Settings
Customers are sometimes unaware of the capabilities of their software because they lack experience with it. Providing this extra customer service can ensure that the consumer is safe throughout the early usage phases.
Use Checklists
Many moving elements must be tracked and monitored while developing safe software. Use checklists to help your team keep track of all essential security policies and procedures at regular intervals, such as weekly or monthly meetings.
Remain agile and proactive
Wise software developers study vulnerabilities, learning their causes, detecting patterns, preventing recurrences, and updating their SDLC with new understanding. They also keep track of trends and update on best practices.
Conclusion
In summary, developing secure software is about more than just safe code. Taking a comprehensive approach and incorporating particular DevOps practices into your routine workflow is imperative. When we say secure DevOps, this is what we mean: from the start of Software Development through deployment and continuing. It guarantees that security becomes a central part of all you do instead of something separate that only gets awareness at specific times or after an invasion.
In the end, coding safely is a never-ending quest. As a result, you should continue looking for new methods to enhance and make your code more secure as technology develops and cyber criminals develop new types of assaults to target.