appdevelopment
devsecops
operations
security
What is DevSecOps?

There are as many as 3 million cyberattacks daily worldwide, which is constantly increasing. In a world where nearly 60% of small businesses have been affected by cyberattacks, security cannot be secondary. Creating the right software and ongoing testing are two critical factors. But even testing software following the best practices is not enough in the face of such a significant threat of cyberattacks.
That's why many software development companies changed their approach to security by implementing DevSecOps. DevSecOps automatically takes care of security at every, even the initial stage of the software development lifecycle, enabling the rapid creation of secure software. Take a closer look at this topic because the issue of security is essential for every, even the smallest, company.
What is DevSecOps?
DevSecOps, an amalgamation of the words development, security, and operations, uses automation to add a layer of security at each step in the software development lifecycle - from design to integration to security testing and deployment. It ensures that your product is thoroughly secure before it ever reaches customers.
By combining Agile development and DevOps workflows with automated IT tools, the innovative methodology of DevSecOps allows for security to be integrated into the product from its conception. This practice ensures that your products are secure at all times by conducting security audits and tests in tandem with project management processes throughout each stage of the development process. In the past, secure code was "bundled" into software at the end of the development cycle, but this solution had many drawbacks.
DevSecOps integrates application and infrastructure security with Agile and DevOps processes and tools. It solves security problems and security vulnerabilities as soon as they appear, so when their repair is easier, faster, and cheaper. In addition, DevSecOps makes application security a shared responsibility of the entire team, not just security teams. Thanks to DevSecOps, secure software is created without slowing down the whole software development process.
Benefits of DevSecOps

Security is a priority for every organization today. Thanks to DevSecOps, application security testing is effective - and equally important - fast because it does not delay the software development lifecycle. Let's take a closer look at some of the main benefits of DevSecOps, thanks to which software development companies more and more willingly implement this solution.
DevSecOps introduces security processes from the beginning of the development process. It is crucial to ensure the final software's high level of security.
During the entire software development lifecycle, security controls are carried out on an ongoing basis to detect possible security vulnerabilities at the earliest possible stage. Of course, any vulnerability or bug found is immediately fixed. Thanks to this, at the last stage of development, there will be no error, the solution of which will be time-consuming and costly or will require radical changes in the project.
DevSecOps offers many testing tools that can be tailored to project requirements and provide a better level of security.
-
Faster Software Development
Some fear a greater focus on security issues will make the development process longer. Meanwhile, using DevSecOps speeds up the entire process and guarantees application security. It is because security issues can lead to huge delays the longer the error is discovered. It, in turn, increases the cost of the project. DevSecOps saves time and costs by minimizing the need to repeat the process to resolve security issues after the fact. Integrating security eliminates repetitive inspections and unnecessary rebuilds, resulting in a secure code.
Automation is a crucial feature of DevSecOps and an essential benefit simultaneously. Each stage has been automated to exclude possible human error. Security testing can be integrated into an automated test suite for operational teams. Automated testing can ensure that built-in software dependencies have the correct patch levels and confirm that the software has passed the tests.
DevSecOps is excellent for repetitive processes. Thanks to this, the applied security measures are consistent throughout the production environment, even when the environment changes.
With a sophisticated DevSecOps approach, your organization will gain the advantage of enhanced automation, dynamic configuration management, orchestration tools, secure containers, and immutable infrastructure techniques that enable serverless computing operations.
Sometimes the communication between operations teams, development teams, and security teams is at a poor level, which can have catastrophic consequences for the project. The contribution of each of these teams is crucial, but the different proposals and innovative solutions of individual teams can be mutually exclusive. The situation will be resolved quickly if the team's communication is at the right level. But if teams don't communicate with each other, it's a simple recipe for failure.
DevSecOps somehow enforces close cooperation of these teams because programming and security issues are combined. Thanks to this, all teams must effectively cooperate and communicate with each other, and the overriding goal is to ensure an appropriate level of security.
How does DevSecOps Work?
DevSecOps aims to ensure security in the software development process most simply and transparently as possible. It can be achieved, among other things, by establishing continuous collaboration between developers, release management (also known as operations), and the security team. The right level of cooperation and communication is essential in each of the 6 stages of DevSecOps.
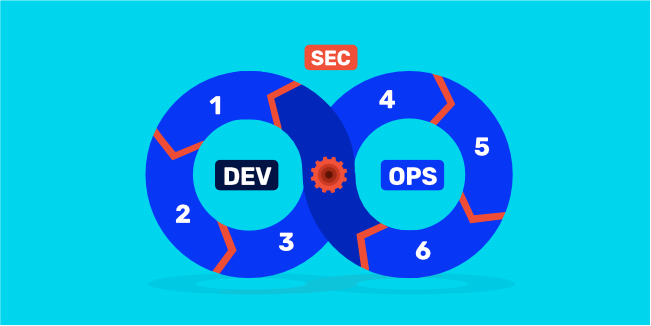
Step 1 - Plan
Planning is the most critical step in DevSecOps and requires collaboration, review, discussion, and systematic security strategy analysis. To successfully implement DevSecOps processes, teams should carry out an extensive security assessment to create a definitive plan that outlines where, how frequently and when cyber safety testing will occur.
This stage is the least automated phase of DevSecOps.
Many DexSecOps scheduling tools (e.g., IriusRisk) make your job much easier. You can also consider using additional tools to manage the process and improve communication (e.g., Jira, Slack). They will be helpful in any project you run.
Step 2 - Build
As soon as developers input code into the source repository, the build stage is initiated. Static code analysis, code reviews before it's committed, and pre-commit interception are critical security processes during this development phase. To enable engineers to author more secure coding, DevSecOps tools are used.
DevSecOps tools strategically prioritize automated security analyses on build output artifacts. Including software component analysis, static application software testing, and unit testing is integral to ensuring optimal security. Additionally, these tools can be harnessed to connect with an existing CI/CD pipeline for easy automation of tests.
While building software, monitoring and scanning third-party code dependencies that may be sourced from unreliable and unfamiliar sources are crucial. These external components may inadvertently or deliberately contain security flaws that could easily be exploited. To ensure the safety of your project, take the time to review these dependencies for any issues before pushing them out into production.
Step 3 - Test
After generating and deploying a build artifact to staging or test environments, the testing phase is initiated. Through Dynamic Application Security Testing (DAST) tools, live application flows like authorization procedures, user authentication processes, SQL injections, and API endpoints are detected. Centered on the security of your web applications - DAST scans for any high-severity known issues that could arise from using it.
Step 4 - Deploy
After passing through previous phases successfully, it is time to launch the build artifact into production. During this deployment phase, special attention should be paid to security that only occurs when a system is live and fully operational. Following thorough testing of both application code and executables during the release phase of the DevSecOps cycle, this stage concentrates on protecting runtime infrastructure by reviewing settings such as user access control, firewall access, and remote management.
Step 5 - Operate
The next critical phase is operation, and the operations team often performs periodic maintenance. On the surface, this phase seems the shortest and least important, but it is not true. Carrying out this step correctly will allow you to enjoy a safe application or software.
Step 6 - Monitor
After launching and stabilizing the application in a working production environment, extra security precautions must be taken. Companies must use automated security checks and monitoring loops to watch for any assaults or information leaks. By consistently monitoring operations, businesses can rest assured their applications are secure from malicious threats.
To discover security frailties, companies may employ an internal or external team of experts to conduct penetration testing by intentionally hacking the system. Alternatively, you can offer a bug bounty program wherein outside individuals are given financial rewards for uncovering and reporting vulnerabilities in your system's protection measures.
Monitoring is the last stage of DevSecOps, but it is as essential as the earlier stages. Therefore, this step should always be completed.
Conclusion
DevSecOps is a process that should be continuously repeated and applied to every new code deployment. While it can pose a challenge, it also brings numerous advantages, such as accelerated releases, minimized bugs and vulnerabilities, and improved collaboration between teams. In light of rising cyberattacks, software must now be developed with security at its core more than ever before. It makes implementing DevSecOps even more paramount.
We hope you found this article helpful in understanding DevSecOps and why you should consider adopting its practices. If you want to talk to our specialists about how they create secure software, make an appointment for a free consultation at a convenient time.